Passwords are one of the fundamental components of securing a system. After all, it is the primary method for a system to authenticate a user. There are other methods, of course, such as biometrics and card keys, but those are either weak (card keys could be easily compromised) or infeasible. Picking a strong password that is known only to the users goes a long way in terms of making a system inaccessible to anyone but you.
Due to their importance, passwords have become the primary target for attackers. If a victim’s e-mail password was compromised, the attacker, for example, can read the victim’s e-mails; send e-mails, impersonating the victim; delete the e-mails; and numerous other attacks. Therefore, it is very important to pick a strong password that is hard to guess by anybody (even people who know you).
Naturally, there are many factors to take into account. For example, is this password protecting your bank account? Or is it just for some mailing-list? You might want to pick a “stronger” password to protect your money than to protect your identity in a mailing-list.
Also, does the system have other defenses and authentication mechanisms besides a password? For example some systems have a mechanism called two-factor authentication, where it is not enough to have a password to access the system. You might also need to enter a verification code sent to your phone,or e-mail. So, in addition to your password, you need access to your phone or e-mail. Having more than one authentication factor might allow for a slightly “weaker” password since there are other hoops that the attacker needs to jump through. There are other forms of authentication such as validating your location or the browser application you are using.
There is also the question that the password picked needs to be remembered. Chase.com, for example, limits what kind passwords you can set, by not permitting you to enter any special characters, presumaby to allow you to remember it easily, and at the same time, their other authentication mechanisms make up for potential weakness.
Let us assume here that what you are protecting is the storage on your laptop. If you want to know what I mean check out this story. In this case, your password may be your ONLY defense mechanism. You want a password that is difficult to guess by anyone (even your closest associates). So, writing it down and keeping it in a closet might not be an option. You need a password that is both hard to guess and hard to forget by you.
Entropy:
Notice that above I put double quotes on “stronger” passwords. This is because we need to know what “strong” or “weak” means. In order to select a strong password we need a measurement on how hard it is to guess it . For example, let us assume you decided to select a password that is one letter. The letter “G”. Represented by computers, this maybe the code “1000111”. As you can see here, there are 7 bits, which means the correct password can be guessed after at most 2^7 tries. This is where entropy comes into action. It is basically an attempt at quantifying how hard it is for a person to guess a selected password.
Building up on the last example, NIST has a desginated an “entropy score” that basically measures how many bits of entropy are needed. Remember, that saying n bits of entropy means that you need at most 2^n tries to guess the password correctly.
In a nutshell, entropy score is giving the following way :
1) The first character gives a score of 4 bits of entropy
2) Chraracters 2-8 give a score of 2 bits of entropy each
3) Chracters 9-20 give a score of 1.5 bits of entropy each
4) After 21 every character adds a score of 1 bit of entropy
5) Special characters and non-alphabetic characters give a bonus of 6 bits of entropy
6) More entropy points may be awarded if the password was verified to not be in a dictionary. However, “dictionaries” in this case are any list that the attacker already has. So it is difficult to measure this. Also, not having a password in a dictionary most likely means that the password is short, since long passwords not part of a “dictionary” are difficult to remember.
Passwords vs Passphrases
From the entropy calculation above it appears that the longer the length of the password the better. This introduces the term “passphrase”.
Key differences between a passphrase and password include:
1) Passphrases allow spaces and all types of characters while passwords may limit what characters are allowed.
2) Passphrases are much longer than passwords
The main point of introducing passphrases is that they are much longer, thus giving more entropy, but at the same time they are much easier to remember than passwords.
This image from xkcd about explains where I’m going with this .
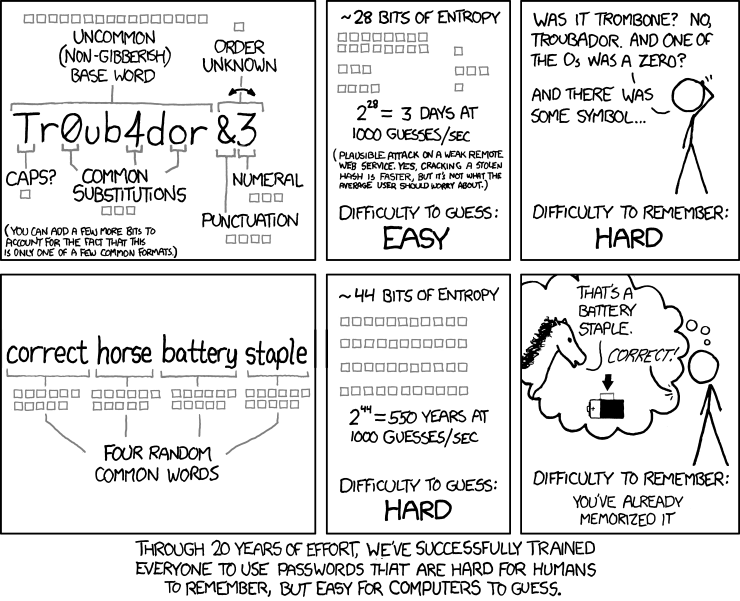
To demonstrate how entropy was calculated here:
passphrase: correct horse battery staple
Using the entropy formula from above we have :
c = 4
orrect = 2×7 = 14
horse batter 1.5 x 12 = 18
y staple 1×8 = 8
4+14+18+8 = 44. 44 bits of entropy
As for the password: Tr0ub4dor&3:
Using the same entropy score calculation we have:
T 4
r0ub4do 2×7=14
r&3 1.5X3=4.5
4 + 14 + 4.5 = 22.5
we also add “6” since that we have a combination of special characters and non-alphabetic characters. So the total is 28.5. Or ~28 bits of entropy.
Which one is easier to remember ?
Diceware
Now this is not the end of the story. Entropy here is not enough, the password needs to be as randomly generated as possible. For example, picking a phrase such as your address might easily be guessed by people who know you.
This is where Diceware comes in. It basically provides you with an option of selecting a password as random as possible yet easy to remember.
Basically, the idea behind it is that you would have a passphrase that is however long you need it to be. Recommended is that your passphrase should be at least 5 words long. If you want it to be really strong, then go for 7. Of course, the longer it is, the harder it is for you to remember.
Diceware basically provides a list of words of 7776 short English words. For every word you want you roll the die 5 times and then map the numbers you have to the word.
In our example here: we will role the die 25 times, because we want 5 words.
Where I get the following:
65341 zig
35115 junk
62353 unify
54466 smut
33541 icky
Well, last step is to come up with a way to remember this passphrae. That really depends on the person. I would usually go with making a correlation between junk, icky and smut. Then remember that unify in the middle. Or something like I took a sharp turn “zig” and landed in junk filled smut that was icky. And hammer in my mind that the word “unify” was in the middle. There might be easier ways to remember. But keep in mind that you may not remember this passphrase if you do not use it a lot. Of course , that goes with short passwords as well.
One thing to keep in mind is that using Diceware limits the set the attacker needs to try out. In this case for example, assuming the attacker knows we picked 5 words. The number of possibilities is calculated as 7776 ^5., which is ~2.8x 10^19. On a modern computer this is still infeasible to break.
Recording the Password:
Now should you write down your passphrases or not? In this case I wouldn’t write it, mainly because I will be using my laptop all the time so forgetting the passphrase is a bit difficult since I’ve used it countless of times. But there may be cases where writing it down is not an issue. For example, a server passphrase for a bank server can be stored in safe box inside the bank. The assumption here is that it is really difficult for a person to break into a bank and access a safe.
This is some hard core info caeser
the entropy calculation is my favorite.
As you said, a strong password is determined by how hard is it to guess right?
I think if we can make a passphrase easy to remember by a human being, we can “teach” a computer how to guess those easy to remember passphrases, thus it doesn’t matter how strong the passphrase really is. Because if human can remember it so does the computer.
Biometrics is the best solution I guess for ultimate security.
Interesting idea….think you’re talking about AI if we’ll be teaching computers easy to remember passphrases